
Cryptocurrencies and “mining” – how does the digging process actually work?
Table of Contents
Let us, therefore, try to explain, in the clearest possible way, how the mechanisms behind the actions of alternative currencies work. To do this, we have to go back a little bit in time — we invite you to… Byzantium!
In the beginning, a brief introduction to the problem that concerns the cryptocurrencies. A crypto valent network consists of computers that connect to each other using a distributed network architecture. This means that there are no main servers and each computer is equal to the other. Let us, however, simplify the situation for a moment…
Byzantine problem with cryptocurrencies
The problem concerning the cryptocurrencies, which was noticed already in 1975, is communication between nodes in the network, the so-called problem of two generals. Let us assume that we have two generals who have to agree on the coordination of the attack on enemy troops. They have their messengers at their disposal. The first general sends his messenger to inform him that he will be attacking at 12:00. He does not know whether the messenger had arrived. The second general answered that he would also attack at 12:00, unfortunately, he does not know if the first messenger returned to the first commander whole and healthy. He sends his own messenger to confirm the arrival of the previous one. The first general confirms that he has received an answer, but again he is not sure whether the messenger will return to the second general. So he sends his own… and so on and on.
Between 1978 and 1981 a problem called the problem of Byzantine generals was illustrated. The authors were Leslie Lamport, Robert Shostak and Marshall Pease. It looked like this:
“A group of Byzantine armies surrounds the city of the enemy. The distribution of forces is such that if all the armies attack together, they will be able to conquer the city. Another way to avoid defeat is to withdraw all armies. The generals of each army have trusted messengers who will successfully deliver every message from one general to another. However, some generals may be traitors trying to defeat the Byzantine army. An algorithm should be developed to enable all faithful generals to agree on a roadmap. The final decision should be roughly the same as one that would be taken by a vote on the decisions of individual generals. If the vote is not decided, the final decision is shall be a retreat.”
The case of the problem of two generals focuses on the problem of data transfer and not on the problem of trust in the source. The Byzantine problem focuses on trust in the source, not trust in the information channel. In a computer network, you can determine whether the server is running or not. If the server is running but not properly — then we have a Byzantine problem. We must then have a solution that allows making the final decision. Thanks to the development of cryptography, this issue is a bit easier. It allows using the digital signature of the message and its verification.
Algorithms resistant to the problem of Byzantine generals (false information) have appropriate implementations, referred to as Byzantine Fault Tolerance (BFT). It can be considered that this is also one of the most difficult problems that can be encountered in algorithmics. Not only must blockchain systems have adequate resistance to such errors, but also all those things that rely on data from a large number of sensors (aircraft, nuclear power plants, space equipment, etc.).
PoW — Proof of Work
Proof of Work was used before Bitcoin, one of the best-known cryptocurrencies. In 1997 Adam Back created the Hashcash algorithm, which was used to limit the number of spam emails sent. Despite this life-enhancing application, Proof of Work has gained its most popularity only with its implementation in Bitcoin. But what is Proof of Work about and what does the crypto mining process have to do with it?
Proof of Work means you have to do the job. In the case of the cryptocurrencies, it is the solving of a certain puzzle. Currently, there are several dozen PoW algorithms: Hashcash, SHA256 Bitcoin, Ethash, Equihash, NeoScrypt and many, many others. But for the purpose of this article about cryptocurrencies let us stay with Bitcoin’s algorithm, so as not to complicate the attempt to explain the topic that we are discussing.
In its original version, Hashcash uses the SHA1 (hash) function, which is 160 bits long. Bitcoin uses double SHA256. SHA256 length is 256 bits. As mentioned above, Proof of Work requires solving a puzzle. A puzzle that needs to be solved in Bitcoin is to find a result of the hash function that is lower than the indicated target.
H(x) < target
It can be said that the puzzle is to find a hash that contains a number of zeros at the beginning. Proof of Work algorithms also have difficulty mechanisms to maintain the average rate of finding a new block (in Bitcoin the average is 10 minutes, in Ethereum 15 seconds). The difficulty was introduced due to the increase in the number of computers that will look for a given solution.
The element that is used in PoW algorithms is the so-called nonce. A nonce is used as a dynamic element that must be found. Every “miner”, having transaction data. tries to guess the appropriate nonce by “sticking” it to the rest of the data. So let us try to show this on an example:
Let’s assume that we are looking for a hash that has 3 zeros at the beginning and that our familiar element (which is transaction data) will be the text: “antyweb”.
The hash of SHA256 for our text “antyweb” is:
3f186f524e5395a9876cb8c900749aba8734bbfa0b7f0b668048531094978477.
As we can see, we do not have the assumed number of zeros at the beginning, so we have to use the previously mentioned nonce. By using a simple bash script let’s try to guess what kind of nonce we need in order to meet the 3 zero condition at the beginning. We will try to do it by iterating nonce from zero to up, i.e. by successively hashing: “antyweb0”, “antyweb1”, “antyweb2” and so on. Using this simple script:
i=0; while true; do echo -n “antyweb”$i | sha256sum | grep -q ‘⁰⁰⁰’ && echo $i $(echo -n “antyweb”$i | sha256sum); ((i++)); done
We will get the result:
5387 000c3d92284057270874106b5912a9b702e70e4ecf63171601780e8528885cb0 –
10794 000818a5f2335f0faa5d4160f10fd83d2017f050f4ced0e6fee8a61eb7cabfa3 –
22248 0009451638cf738b9dfe28c6ee120562ef357a99820f316a7c255877b5bbc51b –
23153 0009cd2f918315e7861bdbd5e357cdbbf7ca629c1f0aa8851e80c908d1e07dd4 –
In the first column, we have the number of iterations required to achieve the desired goal and have 3 zeros at the beginning of the hash. Increasing the difficulty — let’s say we would like to have 4 zeros at the beginning — and by using our script again by changing ^000 to ^0000 we will get:
i=0; while true; do echo -n “antyweb”$i | sha256sum | grep -q ‘⁰⁰⁰⁰’ && echo $i $(echo -n “antyweb”$i | sha256sum); ((i++)); done
39775 00005e15dee9ac46e24649cf59872b2995d24095f6264cc833fc5c609d50c5bb –
136342 00000d68cc0824adca5cc9c5bd586a178fca91b07f91254ec33981bad951415b –
145097 00007108f76396d6dfa8f064834e1e2f62ff1e8613ed4c574d0d0ebb93d54747 –
256406 000003f21497e0f69016bba19685f4dd5e7178619d4a7f1258ea38b7f718df5a
While in the first example we obtained the result after 5387 iterations, in the second one we had to perform 39755 iterations. By putting all of this together as “antyweb39775”, we achieve our goal. If we wanted to have five zeros at the beginning, we would need 136342 iterations, as can also be seen from the example above. If you want, you can check what will happen if you set our nonce to 17031805.
We must also point out that we have applied some simplification here. We display the data in the hexadecimal system. Ultimately, however, it is a binary system, and “miners” are looking for zeroes in bits (more precisely, H(x) < target). Initially, it was searching for zeros in the initial 32 bits from a total of 256. now it is about 72 bits, which are zeros at the beginning of a given hash.
In a distributed network, such as cryptocurrencies networks, each of the miners tries to be first and works on a similar set of data. Transactions selected by miners depend on the fee that the person ordering the transaction has set. The result is a network performance that is slow (8–15 transactions per second compared to about 50,000 that can be handled by e.g. VISA) for everyone to work on more or less the same “task”. In such a situation, blockchain’s fees for transactions increase.
The excavated block is then sent by the miner to the next nodes in the network. Each of them verifies its validity: if it is correct, it sends it further to known nodes; if it is incorrect, it rejects it and simply does not send it further.
PoW algorithms were initially run on a PC and used only a processor (CPU) for their tasks. With time, the algorithms were migrated to work on graphics cards (GPUs), and nowadays, specialized devices dedicated to PoW algorithms (ASICs) are being developed very dynamically. For example, Bitcoin has already built ASICs, which have been on the market for several years. As a result of the introduction of ASICs to the market, it has become unprofitable to dig bitcoins for the GPU. Recently, speculations have also emerged that one of the ASIC companies has built a device (and has it on offer in the pre-order) for Ethereum as well. The fact that Ethereum and its Ethash algorithm are so interesting adds to the spiciness of the case that Ethash has high requirements for RAM bandwidth and is supposed to be an algorithm resistant to dedicated devices (the so-called ASIC-resistant).
Since Ethereum does not have (yet?) ASIC devices on the market, its “extraction” takes place mainly with the use of graphics cards. As probably all those who are interested in the technology industry have heard, graphics cards have become difficult to access and their prices have risen over the past twelve months. The interesting thing in the world of Ethereum is that the community wants to change the algorithm from Proof of Work to Proof of Stake. Rumors about ASIC also caused the community to want to run a hard-fork modifying the algorithm so that ASIC PoW would be useless in this network. Potential appearance of ASIC may cause faster migration of Ethereum to the PoS algorithm — we will certainly follow this topic with a lot of interest.
The use of a large amount of computer equipment (mainly GPUs and ASICs) resulted in an increase in the use of electricity. The current use of electricity by the bitcoin network is projected to be higher than the annual consumption… of Ireland and the Czech Republic, at around 70.25 TWh!
PoS — Proof of Stake
The growing popularity of cryptocurrencies and the increasing use of equipment, and consequently electricity, have shown that it is necessary to look for other solutions. Solutions that will allow minimizing electricity consumption and easier adaptation of technology by companies from different industries. One alternative is the so-called Proof of Stake (PoS).
Proof of Stake is a transaction confirmation mechanism that uses “the state of possession”. In the case of PoW, a miner who has more computational power simply earns more. A user with a six-card excavator will have more profit than a user with a single graphics card. In the case of PoS, confirmation of a transaction and a block takes place by drawing a user from a specific pool. It is assumed that this pool consists of users who have declared some (or all) of their coinage in favor of being a so-called Validator. A person who has more coin deposits will have a better chance of being drawn (the person drawn will create a new block and will receive a prize for it, as well as fees for transactions — as is the case with the PoW algorithm).
DPoS — Delegated Proof of Stake
Delegated Proof of Stake is a kind of Proof of Stake. It is designed to be more democratic and fairer and more effective than other methods. Network users who use the DPoS as a consensus algorithm vote for a so-called delegate/ witness. This creates a group that is privileged to approve transactions and blocks. Unfortunately, to some extent, the structure of the network is changing and becoming decentralized rather than distributed. The advantage of DPoS for cryptocurrencies may be achieving faster operation in terms of supported transactions per second, but this is done at the expense of centralization.
PoA — Proof of Authority
The Proof of Authority consensus mechanism is mainly used in networks that require user authentication. This is because in PoA the identity of the user must be known. For the network used by cryptocurrencies, this means that only trusted computers (people) can use its resources. If this trust is broken, the network may block access to the user. In PoA we can find full centralization, as this algorithm can be used in closed solutions (private blockchain). Of course, there is also an option for decentralization, where the network community chooses trusted persons — just like in DPoS (however, DPoS can be anonymous).
Cryptocurrencies – consensus and trust
The beginning of the article about cryptocurrencies presents a problem that all consensus algorithms have to face — Byzantine Fault Tolerance (BFT). People interested in cryptocurrencies actions certainly had the opportunity to meet this term more than once. What does the introduction of tolerance against the problem of Byzantine generals prevent us from? Mainly before users who try to force the network to the disadvantage of others, and attempts of embezzlement. As a result, it also protects against 51% attacks.
Let us stop here for a moment at an attack of 51%. In PoW algorithms, in order for such an attack to be successful, it is necessary to have most of the computing power. It is then possible to make incorrect transfers or reversals of the network backward (as was the case with Bitcoin Gold). In the case of PoS, the attacker would have to have a majority share in the total coinage. Many people believe that a person with a 51% share in the network in the form of coinage will not benefit from it for a simple reason — they would attack their own network.
What, then, is a consensus? Can it be said that it is PoW (PoS, etc.)? Unfortunately not — the algorithm alone is not a consensus. In order to better understand this issue, we need to return to the very architecture of the network. Cryptocurrency networks are usually distributed networks. The miners themselves will not reach a consensus (although this may be the case in a utopian situation in which every node is a miner). The situation can be described in the following picture:
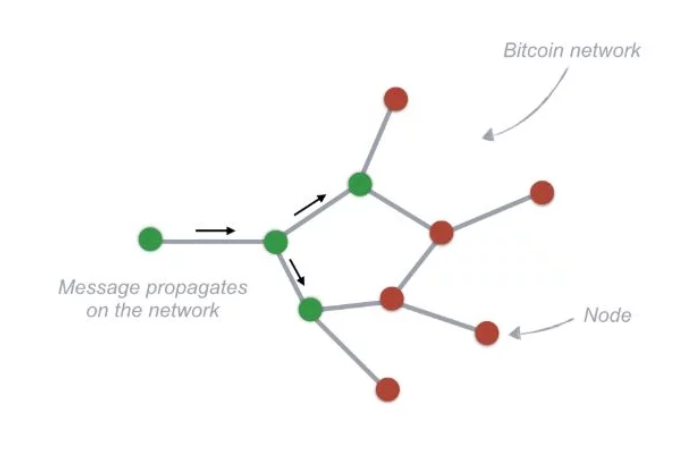
The miner digging out the new block sends it to the Internet. The communication speed may vary between nodes in the network. Thus, it may be that two miners will extract the block in a similar period of time. While waiting for the next block, he will win the part of the chain that will be longer (someone will extract the next block and send it to the network). However, the consensus is also not about which chain is the longer one. Consensus on the web is nothing more than an agreement between nodes in the web — those who copy and those who verify transactions and send them on to the rest — about the principles of operation.
An example is the agreement to introduce new functionality. If ordinary nodes so wish, and miners do not, they may no longer accept blocks sent by miners. So both parties have to agree which blocks are correct and when (and this means that the nodes have to comply with the network protocol).
We hope that we have managed to explain how the mechanisms behind the actions of cryptocurrencies work and to show you how consensus algorithms work in blockchain networks in a relatively understandable way. Of course, using some simplifications, because the technical algorithms of extraction or signing the block and its dissemination in the network (together with validation of correctness) may be much more advanced 🙂
This may interest you:
Concise Software among the best blockchain developers in Poland!
Blockchain in healthcare – here are 5 essential use cases
10 Use Cases of Blockchain in Banking
How are we all going to use blockchains in the near future?
Blockchain – a starter guide to the world of technology
Introduction to a smart contract on blockchain
Everything you need to know about Ethereum
Open banking – a new dimension of financial services
Smart contracts – what are they and how to create them? [GUIDE]
P2P payments – what are peer-to-peer payment apps used for?
What is an Initial Exchange Offering (IEO) and how to participate in it?
IEO vs STO – key differences you should know
What is blockchain development? A complete guide!